In an environment with a vCenter Server Appliance (VCSA) 6.5.x, 6.7.x or vCenter Server 7.0.x, you experience these symptoms:
- The vmware-vpxd service fails to start.
- Logging in through the Web client display errors similar to:
In the /var/log/vmware/vpxd-svcs/vpxd-svcs.log file, you see entries similar to:
ERROR com.vmware.vim.sso.client.impl.SecurityTokenServiceImpl$RequestResponseProcessor opId=] Server rejected the provided time range. Cause:ns0:InvalidTimeRange: The token authority rejected an issue request for TimePeriod [startTime=Thu Jan 02 09:22:13 EST 2020, endTime=Fri Jan 03 09:22:13 EST 2020] :: Signing certificate is not valid at Thu Jan 02 09:22:13 EST 2020, cert validity: TimePeriod [startTime=Wed Jan 06 20:44:39 EST 2010, endTime=Wed Jan 01 20:54:23 EST 2020]
Note: The endTime should be a date in the past if the certificate is expired.
Logging in to the vSphere Client fails with the error:
HTTP Status 400 – Bad Request Message BadRequest, Signing certificate is not valid
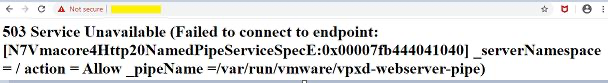
Logging in through the Web Client displays a message similar to:

- Replacing any certificate on either PSC or VCSA fails.
- Adding, modifying or deleting registrations from the Lookup Service manually using the lsdoctor tool fails.
- Deploying a new PSC and doing a cross-domain repoint fails.
- Deploying a new PSC as a replication partner on the existing SSO domain fails.
- Connecting services with VCSA fails with vpxd authorization errors similar to:
Logging in through the Web client displays errors similar to:
Cannot connect to vCenter Single Sign-On server https://VC_FQDN/sts/STSService/vsphere.local
OR
Cannot connect to vCenter Single Sign-On server https://VC_FQDN:7444/sts/STSService/vsphere.local
OR
[400] An error occurred while sending an authentication request to the vCenter Single Sign-On server 2020-10-07T08:27:51.547Z info vpxd[12853] [Originator@6876 sub=vpxCryptopID=SWI-7203af8f] Failed to read X509 cert; err: 151441516- trying to export a VM as OVF fails, and
/var/log/vmware/content-library/cls.log contains the following error:
[2023-04-06T16:47:24.409+02:00] [INFO ] http-nio-5090-exec-1022 70179544 103561 ###### com.vmware.vise.security.spring.DefaultAuthenticationProvider Session initialization complete for sessionId 103561, clientId 200264
[2023-04-06T16:50:00.540+02:00] [INFO ] http-nio-5090-exec-1022 com.vmware.vapi.security.AuthenticationFilter Authentication failed com.vmware.vapi.std.errors.Unauthenticated: Unauthenticated (com.vmware.vapi.std.errors.unauthenticated) => { at com.vmware.cis.data.service.session.SessionAuthenticationHandler.authenticate(SessionAuthenticationHandler.java:36) at com.vmware.vapi.security.AuthenticationFilter.invoke(AuthenticationFilter.java:233)Note: The preceding log excerpts are only examples. Date, time, and environmental variables may vary depending on your environment.
Resolution
Purpose
This article provides steps on regenerating and replacing expired Security Token Service (STS) certificate in VCSA 6.5.x, 6.7.x and vCenter Server 7.0.x using a shell script.
For steps on regenerating and replacing STS certificate in VMware vCenter Server 6.5.x and 6.7.x installed on Windows using a PowerShell script, see "[Signing certificate is not valid" error in vCenter Server 6.5.x and 6.7.x on Windows](https://kb.vmware.com/s/article/79263).
For more information on STS certificates, see Security [Token Service STS](https://docs.vmware.com/en/VMware-vSphere/6.0/com.vmware.vsphere.security.doc/GUID-18482A49-F9F8-4755-9113-3ADBAFE74EA3.html)
Cause
This issue occurs when the Security Token Service (STS) certificate has expired. This causes internal services and solution users to be unable to acquire valid tokens and, as a result, fail to function as expected.
**Note**: When the STS certificate expires, it does so without warning. On some systems, this expiry may occur as soon as two years from the initial deployment.
The following scenarios can cause STS signing certificate to expire at 2 years:
- Fresh PSC/vCenter Server 6.5 installation starting with U2 or later (6.5 only).
- Fresh installation of PSC/vCenter Server 6.5 U2 or any later 6.5 releases and upgraded to a later version including 6.7 and 7.0.
- STS signing certificate has been replaced using certool post-installation of PSC or vCenter Server.
- STS signing certificate has been replaced with custom certificate (Internal/External CA Signed).
Impact / Risks
Warning
This script interacts with the VMDIR's database. Before running the script, take an offline snapshot concurrently for all vCenter Servers and Platform Service Controllers in the SSO domain. Failing to do so may result in an unrecoverable error and require redeploying the vCenter Server.
Notes:
- This script should only be run once per SSO domain.
- In environments containing Horizon View, see [Connection Server unable to accept vCenter thumbprint with an error "There was an error identifying the validity of the server" (67701)](https://kb.vmware.com/s/article/67701).
Resolution
To resolve the Signing certificate is not valid error:
- Download the attached fixsts.sh script from this article and upload to the impacted PSC or vCenter Server with Embedded PSC to the /tmp folder.
- If the connection to upload to the vCenter by the SCP client is rejected, run this from an SSH session to the vCenter:
chsh -s /bin/bash

